Via Privacy Hub
Malala Yousafzai – the Nobel Peace Prize-winning activist – once famously wrote, “One child, one teacher, one book, one pen can change the world.” Had Malala said this nowadays, she could very well have added: “one 2FA-locked smartphone, one encrypted messaging service, one robust VPN” – to name a few recent safety measures needed for today’s activists.
Indeed, the list of protections that activists must use online is growing, and with good reason. It’s increasingly difficult to maintain your online privacy, as technologies (and those who control them) advance and encroach upon their users.
The good news is that many of the precautions that activists can take online are relatively simple to adopt. We’ve compiled a handy Activist’s Guide to Online Privacy and Safety here, to help you navigate through your options – freeing up more time for the pursuit of your causes.
Before we dig in, let’s looks at some recent and influential movements, that are drawing activists to action:
What do the above movements have in common today? The internet. The fight for all causes has become fully digital, and this means everything you do online – from organizing rallies or protests, sharing campaign materials, or just expressing your opinion – could now be monitored or even be used against you by those who oppose your cause.
If you’re called to activism – either as a participant or an organizer – it’s more important than ever to protect your online privacy.
Why Is Protecting Online Privacy Important for Activists?
As an activist, you’re likely attracting attention in the name of your cause. This means you could often land yourself on the radar of government officials or law enforcement agencies – and you might also be monitored by your opponents, rival groups, and informants.
With surveillance technology more widely available, such bad-faith actors can easily gain a complete picture of your online and offline activities. In other words, what you do online can have serious real-world implications.
Take the rather extreme case of Roman Protasevich – the exiled, Belarusian activist – who used Telegram to coordinate protests in opposition of the Belarus government in 2020 and 2021. In May 2021, Protasevich’s Ryanair flight from Greece to Lithuania was forced by a Belarusian fighter jet to divert and land in Minsk, Belarus. Protasevich was arrested upon landing.
The following day he appeared on Belarusian state TV confessing to “organizing mass unrest”. He had marks on his body, leading to the widespread belief that Protasevich had been tortured. He has since been confined to house arrest in Belarus.
Belarusian authorities were able to track Portasevich through his online presence, follow his travels, and then pursue his arrest. The lesson is: if you post something on social media that is critical of those in power, you’re likely being noticed by more than just your followers.
It is therefore imperative that, as an activist, you’re taking steps to protect your online privacy and safety.
What Are the Biggest Risks to Online Privacy for Activists?
There are six major areas of digital risks that can impact you as an activist. They are: government surveillance; internet connection privacy; website privacy; data privacy; device and account security; and communications and social media. We’ll explore each of these areas in full, but here’s a top-level summary:
Risk: Government Surveillance
As mentioned, if you’re an activist in the public eye – e.g. active on social media, speaking at conferences, visibly engaged with civil society organizations – you may become a victim of targeted government surveillance, especially if you’ve openly demanded reform, promoted human rights, or exposed potential corruption or violations.
Voicing concerns about your government’s policies and conduct is never going to make you popular with the authorities. This is most problematic in countries with dubious records of cyber-surveillance – you’ll need to be extra careful if you live somewhere that regularly disregards individual rights. This is not limited to countries with authoritarian regimes, however.
Thanks to Edward Snowden’s 2013 leaks, we’ve learned the extent to which governments of all types circumvent privacy protection laws to monitor their citizens’ online activity.
Worryingly, you don’t have to have done anything wrong to be the subject of targeted surveillance. The more recent Pegasus spyware scandal has shed light on how – from Mexico to the Middle East – governments use a range of sophisticated cyber tools to spy on a number of professionals including journalists, educators, and even government officials themselves.
Through surveillance mechanisms, authorities have been known to access devices, retrieve contacts, uncover passwords, monitor texts and phone calls, and interfere with activists’ work.
This sort of activity has also bordered on nefarious, as governments have used the information collected through surveillance means to smear activists, rebrand them as criminals, and fabricate charges to have them arrested.
TARGETED SURVEILLANCE: Ahmed Mansoor
A human rights activist in the United Arab Emirates, Ahmed Mansoor called for progressive political reforms. In response, the UAE state security apparatus allegedly hacked his phone, computer, and even bank account, before arresting him for questionable charges that resulted in a 10-year prison sentence.
The Effect of COVID-19 on Digital Surveillance
Governments in at least 25 countries have implemented large-scale surveillance programs, since the onset of the Covid-19 pandemic. There has been an unprecedented increase in digital surveillance, including mobile data tracking, apps to record personal contact with others, tracking of medical records, and CCTV networks with facial recognition.
With billions of people facing enhanced monitoring, abuses of power are a big concern if the proper safeguards aren’t there. Researchers and privacy advocates say it will be difficult to roll back the increased surveillance.
These methods have been adopted by democratic and authoritarian states alike. In Western democracies, this surveillance tech is likely to be under greater public scrutiny, but it remains to be seen if your personal and health data will remain private and unexploited once the pandemic subsides.
How to Protect Your Online Privacy
Activists like you may feel that protecting your online privacy is a daunting task, especially after reading about all the possible threats. Know that you can do several straightforward things to protect yourself – from securing your internet connection by using a VPN, to safeguarding your social media and mobile devices.
Risk: Internet Connection Privacy
What Your Internet Service Provider (ISP) Knows
Your ISP handles all of your internet traffic, so it’s able to monitor and track everything you do online. Your ISP can potentially see what you order online, your passwords, your emails, all your files, and even what you ask your smart speaker.
What’s worse: your ISP can collect enough personal data on you to link your various activism activities, possibly helping authorities to build an incriminating case against you. ISPs claim they don’t send your data to third parties, but they can be compelled to hand over your data to law enforcement and government agencies.
In Australia, for example, ISPs have been ordered to provide federal police with user browsing history. Some of that data is stored for up to two years.
Use A VPN for Secure Connections
To combat the intrusiveness of ISPs, your best bet is to consider investing in a trustworthy VPN (Virtual Private Network). A VPN will help anonymize your internet activity and provide you with a private, secure connection when you go online. VPNs are quite easy to set up and use multiple layers of protection, including:
Encryption
Premium VPNs protect your connection with robust 256-AES encryption. This prevents prying eyes from tracking or snooping on your internet activity. This means your ISP and other third parties won’t be able to see the websites you visit or the services you use.
No-logs Policy
Choose a VPN with a strict no-logs policy because that VPN won’t be able to store any of your user data on its servers. This includes your personal and browsing information. If authorities request any information on you, the VPN won’t have anything to hand over.
IP Address Masking
Larger VPNs have thousands of servers all over the world. When you connect to one, the VPN IP address you’re connected to masks your real IP address. This makes it impossible for anyone to trace your internet activity back to you.
THE DISADVANTAGES OF A FREE VPN
Dozens of free VPNs promise to protect your privacy and sensitive data online. Many of them come with major disadvantages and dangers, including:
-
- Third-party trackers embedded in their software
- Limits on the data amount you can use and number of devices you can protect
- Minimal server options
- Slower internet speeds when using the VPN
- Hidden malware and adware
- Pop up ads, suggesting your data is shared with third parties
Circumventing Online Censorship
If you live in a country with strict online censorship, you’re probably unable to access certain news websites, apps, or social media. A robust VPN allows you to connect to servers in countries where those sites and apps aren’t subject to censorship.
By changing your digital location, you can access geographically restricted content, access unbiased resources, and even organize your activism online. Not every VPN unlocks every restricted content, so best to check which ones work best in your location.
Enhanced Security
Most premium VPNs can be used on major desktop and mobile operating systems. You can even use them on routers, smart TVs, and a few other connected devices. You can also combine a VPN with the other resources in this guide, providing all-around device security.
Use the Tor Network for Anonymous Internet Access
Tor (The Onion Router) is a great way for activists to get online securely and anonymously. When you’re connected to the Tor network, none of your internet activity or data can be traced back to you because it’s all encrypted several times.
We recommend using a VPN and Tor together for maximum privacy and protection. You should connect to a VPN first and then to Tor (VPN over Tor). This way, you get all the privacy protections of the Tor network, and the Tor node won’t be able to see your home IP address. Other benefits of using the VPN over Tor protocol include:
-
- Your VPN encrypted traffic prevents your home network from detecting you’re using Tor.
- A VPN can grant you access to the Tor network in countries and establishments where it is blocked.
- Your VPN won’t be able to see what you’re doing within the Tor network.
- If the Tor browser has a bug, your VPN provides an extra layer of security between you and the bug.
Stay Safe on Public Wi-Fi
Using public Wi-Fi is risky – the traffic that flows through an open Wi-Fi network is usually unencrypted, meaning it’s an easy target for online snoops. If you have to use a public network when engaging in activism-related activities, then it’s imperative that you protect yourself.
Risk: Website Privacy
Browsers
Your standard web browser routinely collects and retains information about your connection and internet activity. The information your browser shares with the websites you visit includes:
-
- Your IP address
- The name of your browser
- The type of device you’re using
- Your cookie settings
- Your browser plugins
- Your mouse clicks and movements
- Where you are and your time zone
- Other basic information including your screen resolution and battery level
Most of this information may seem trivial, but the combined data creates a unique digital fingerprint that websites use to identify you and track you online.
Even if you’ve cleared your cookies (small data files that websites store on your device), history, and cache – or are using an incognito/private window – your browser fingerprint will be visible to websites and third-party analytics. This can potentially create direct links between you and your activism activity.
You might think that simply changing your browser settings to improve privacy will help prevent tracking. This could actually make your browser fingerprint even more unique.
How to Browse Privately and Anonymously
We highly recommend installing browser extensions or switching to a browser that gives you more control over your privacy, to limit your exposure when browsing the web.
If you’re reluctant to change your web browser, you can do a few things to limit the amount of tracking and the data stored on your online activity, including:
-
- Regularly clearing your cache and cookies to limit your risk of being tracked;
- Limiting the number of cookies you accept; and
- Configuring your browser to block tracking ads and invisible trackers.
These steps will help, but they don’t do much to improve your browser fingerprint. As mentioned, configuring certain settings could actually make your browser fingerprint seem even more unique to the websites you visit.
An effective way to lower your browser fingerprinting risk is to use the Tor network. All Tor users should have the exact same browser fingerprint, no matter what device or operating system is being used. You can configure a browser to access the Tor network, or simply use the Tor Browser.
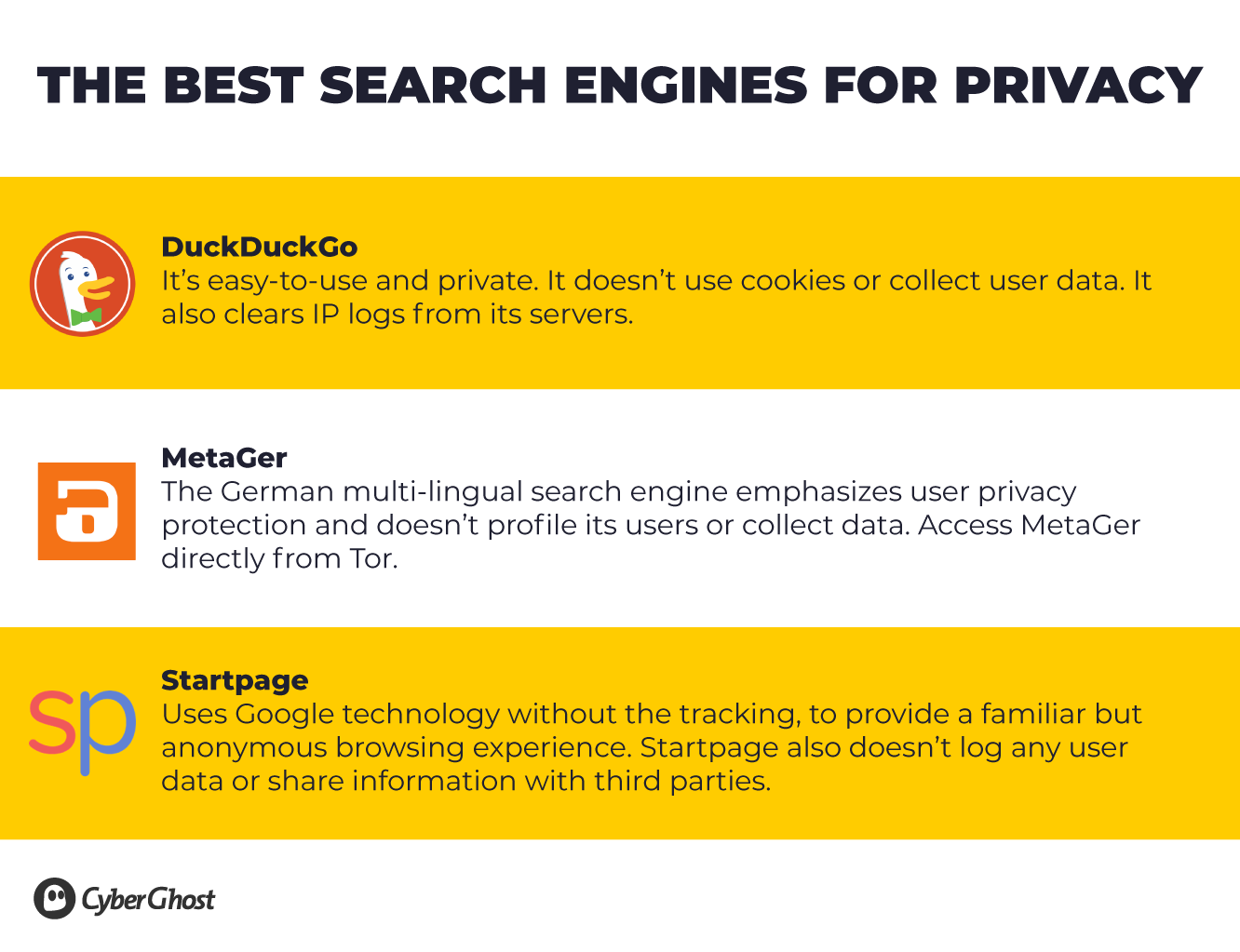
Search Engines
You’d be surprised by how much Google and other search engines know about you. They record a vast amount of data to create targeted ads and personalize your web browsing.
You should know that most search engines can be compelled by law enforcement or government agencies to hand over your search and browsing data. If you’ve regularly searched for information about dissidents and government officials, or looked at legal support and international organizations, think about what this could mean for you as an activist.
We know that Google is the go-to search engine for most people. But it’s one of the worst when it comes to tracking and mining user data. A recent investigation by the Associated Press found that Google still tracks your location even if you disable the ‘Location History’ feature.
Risk: Data Privacy
Activists are often repositories of crucial information, and many sit on a wealth of resources that can help progress their causes. These resources, stored in the form of data, can be vulnerable to malignant attacks from many of the aforementioned bad-faith actors.
Encrypted flash drives (memory sticks) and hard drives are one option for securely storing your data – but storing files onto physical formats may make your data even more vulnerable to theft, loss, or technical glitches. Physical devices also have finite storage capacities.
For this reason, cloud storage has become all-important. Data in the cloud is also more shareable – an important trait for activists needing to divulge materials to promote their causes.
Cloud Storage
We should start with a caveat: just because your cloud storage service provides encryption for your data, doesn’t mean your privacy is guaranteed. Encryption alone won’t safeguard against adamant prosecutors, who may compel large cloud services to cooperate – some services have been known to share data and files with government intelligence agencies like the National Security Agency (NSA) in the United States.
Securing Cloud Storage
You can secure your cloud storage by choosing a provider that encrypts your files locally on your device before they’re uploaded to the cloud (as opposed to files that are encrypted in transit to the cloud). Remember that providers may have means to access encryption keys and can decode or hand your files over to the authorities if legally required.
A highly recommended alternative is to manually encrypt your files yourself before uploading them to a cloud service. That way, you’re the only one with the key to decoding your files – just be sure to never upload the encryption keys with your files.
There are several free and paid encryption apps available but check that they are compatible with both your cloud storage provider and your devices. Make sure the app uses end-to-end encryption, which means your files are encrypted before they leave your device and will stay that way until you access them again.
Risk: Device & Account Security
Mobile Devices
A careful activist will put measures in place to protect laptops, tablets, and phones. However, there’s still a great deal of information that’s given away when using mobile devices:
-
- Texting and phone calls
- Internet searches and visiting websites
- Sending and receiving emails
- Mobile banking
- Posting on social media
- Storing photos, files, and apps using Dropbox, Google Cloud Storage, etc.
The GPS functionality and location services on your mobile devices can also be used to track your movements, even through your social media posts. Government agencies and law enforcement can and often do request this information from telecom providers. What would they discover if your location data were handed over?
A WORD ABOUT SIM CARDS
Mobile phones and privacy don’t mix. Instead of using your regular phone for activism, you could use a secondary phone with a prepaid SIM.
Register your prepaid SIM online with a VPN to protect your privacy.
Tracing a secondary phone is still going to be easy. But the point is to disassociate you from the phone, so be sure you:
-
-
- Can’t be linked to the phone’s purchase or activation
- Don’t install anything on the phone that can be used to identify you, like social media apps or your personal email account
- Disable any communication-related features that don’t relate to texting or calling
- Turn off the phone’s Wi-Fi and Bluetooth
- Turn off the phone when you’re not using it
-
Use the Access Passcodes for Devices
Apart from the passcode, many smartphones now come with biometric unlocking features through fingerprints and facial recognition.
While biometric unlocking is an amazing piece of technology, it makes it easy to access your phone if you’re ever apprehended – just a quick press of your thumb or a point of the phone in your direction and your devices will be unlocked.
You would have to be compelled to hand over a passcode, which is a lot harder.
Two-Factor Authentication
Add an extra layer of security to your accounts by enabling two-factor authentication (2FA) whenever possible. It protects you if someone tries to access your account from a new device, even if they have your login credentials. A text message with a six-digit authorization code is a common form of 2FA. It’s sent after entering your login details.
Update Security Software
Good mobile security software includes the option to remotely delete data from your devices at the click of a button. This is very useful if your phone is lost or confiscated by authorities.
To continually ensure the security of your mobile, you should update your software whenever new updates are released. These updates often include security patches that fix previous vulnerabilities to your software, making phones less vulnerable to breaches.
MORE DEVICE SECURITY TIPS
-
-
- When traveling or visiting courts/government buildings, avoid keeping sensitive or private information on your devices in case they get scanned at security checkpoints.
- Scan external devices and USB sticks for spyware and other malware before plugging them into your computer.
- Check the credentials of anyone tasked with fixing your devices.
- Avoid leaving your devices unaccompanied for long periods.
- If you need to leave your devices unattended, remove any sensitive and personal information (or at the very least ensure they are locked and password protected).
-
Apps
THE WORST APPS FOR PRIVACY
FACEBOOK Wants to fully access and control your device. It claims it’s necessary for app functionality.
FACEBOOK MESSENGER Doesn’t use end-to-end encryption for your private messages, which are likely stored as plain text on its servers.
WEATHER APPS Access your location to provide you with the weather, but then track your location 24/7.
MOBILE MULTIPLAYER GAMES Many gaming apps log huge amounts of your personal data, including your contacts, location, name, and content of messages you share with other users.
Check App Permissions
If you think it’s strange that certain apps (like some of the games mentioned above) need to access your contacts, photos, or location, you’re not alone. It’s surprising how many apps and websites request these permissions by default during installation when they’re not needed for the app to function.
Check your app settings and turn off any unnecessary permissions, particularly your location. This will prevent your physical location from being logged, for example at protests, vigils, and demonstrations.
Delete Old Apps from Phones
If you don’t use an app anymore, get rid of it. Delete the account you used to set it up and then the app itself.
Account Security
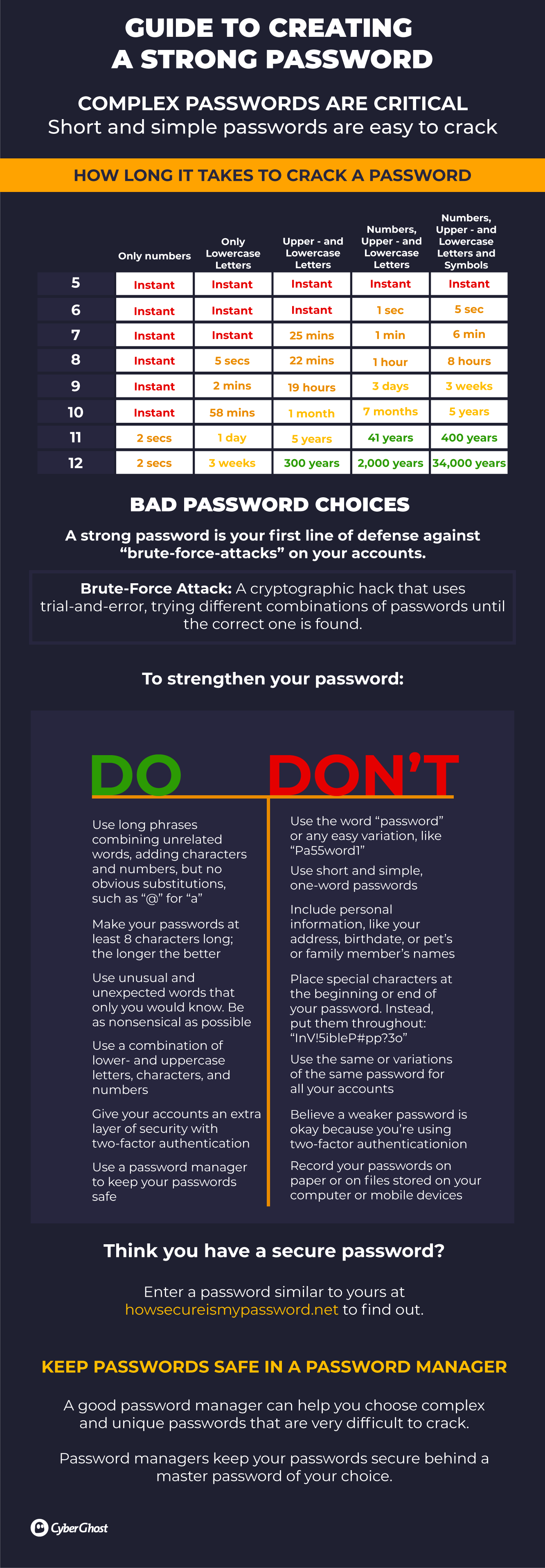
Securing your devices and accounts is of utmost importance, and one of the simpler ways that activists can safeguard their online privacy.
Having strong passwords and passcodes ensures that no one can access your data and accounts if your devices are confiscated or end up in the wrong hands.
Risk: Communications & Social Media
Use Encrypted Communication
Activists often share sensitive information – with lawyers, journalists, organizations, and other activists. Talking face-to-face is the best way to have a truly private conversation, but, of course, this is not always an option.
When communicating online it’s best to use encrypted communication platforms, such as Signal, Wire, and Keybase. This way what you say is protected with end-to-end encryption.
Be advised that Telegram has been subject to data breaches and end-to-end encryption is not enabled by default, except for ‘secret chats’ and video and voice calls.
Most popular email providers are very secure, with iron-clad protocols in place to prevent data leaks. But these protocols aren’t fail-proof. If your email provider is compelled by the authorities to hand over information contained in your emails, it’s unlikely that security mechanisms will protect you.
Maintaining a Private Email Identity
To minimize government authorities snooping around in your emails, you should take extra steps to protect your privacy. Encrypting emails is time-consuming and difficult, so the most practical solution is to use a private email service, like ProtonMail, Fastmail, or Zoho Mail.
Secure email providers designed for activists, including Rise Up and Aktivix are free as they’re funded by donations. But they don’t support the same volume of saved emails as paid providers, so you may need added email management – for example, saving older emails in secure cloud storage.
It’s best to keep your personal email and activism-related email accounts entirely separate. This way, the account(s) you use to organize events or engage with other activists cannot be linked to an account that contains your personal, identifying information.
GENERAL EMAIL SAFETY
-
- Phishing is a type of scam where cyber criminals or other online snoops impersonate legitimate organizations or people you know, usually via email. The idea is to trick users into handing over their personal emails or other private information.
- Scammers may also encourage you to download genuine-looking files or click on links, to get you to install malware or spyware onto your devices.
- Never click on links or downloads sent via email from someone you don’t know. Always check the sender’s email address to ensure it’s legit.
- If you receive an email alerting you of a problem with an account, don’t click any links in the email. It’s best to go to the service website or app directly.
- Note that bad-faith actors targeting activists may use any of the above methods to gain access to your email accounts.
Social Media
While social media offers some of the most useful tools for activists – mass engagement for movements and causes, event promotion, or outreach and campaigning, for example – the companies behind the most prominent social apps and sites have been dogged by controversy, especially concerning privacy and security.
For example, in recent years, the Cambridge Analytica scandal exposed how Facebook allowed the harvesting of personal data from millions of users. Privacy breaches like this show just how much social media knows about you. It’s also clear the information you share through these platforms isn’t as private as you might think.
Social media regularly uses geotagging to track your exact location. Facebook doesn’t just track where you go; it also collects data on what you buy, what you browse, and who you know and talk to. That’s why the platform routinely requests access to your contacts, call logs, and SMS.
WHAT YOU SHOULD KNOW ABOUT FACIAL RECOGNITION
Surveillance dangers are increasing with pervasive and involuntary facial tagging.
Did you know?
-
-
-
- Social media photo-sharing tools have built-in facial recognition software.
- Platforms are building up vast databases that contain images of user faces.
- Law enforcement routinely requests facial profile data from social media.
- All your photos become the platform’s property once they’re uploaded.
- Existing facial recognition programs have no opt-out option. Once you’re in, you’re in.
-
-
Facebook and other social media platforms have repeatedly proven that your personal data isn’t safe in their hands. The more personal information you make available on social media, the greater your privacy risk. For prominent activists, this is a double-edged sword between engagement and exposure.
Change Your Social Media Settings
As an activist, you should always customize your privacy settings from the platform defaults, to ensure maximum anonymity. This will enable you to decide who can view your profile, posts, location, photos, contact information, and if people can tag you or find you in profile searches.
You should also optimize your social media security settings. This is where you can set up two-factor authentication, block profiles, and get notifications when there has been any unauthorized attempt to access your account.
CREATING A SECURE SOCIAL MEDIA ACCOUNT
-
- Don’t use your real/full name
- Sign up with a separate email address from your personal one
- Don’t provide more information than necessary
- Choose a profile picture that can’t identify you or your location, either visually or with meta tags
- Choose a strong password and enable two-factor authentication
- Select false answers for password recovery sections and store your answers in a password manager
- Install a browser extension that blocks trackers and third-party cookies.
To fully understand your Social Media settings you may have to dive into the terms and conditions or privacy policies – this can be tedious and cumbersome (sometimes policies are deliberately murky).
Note that the most important sections are the ones that describe how your data is used when it is shared with third parties, as well as how the platform responds to requests from law enforcement.
Also remember: privacy settings are subject to change. Pay attention to updates to see if any previously private data could now be shared – but also check if additional settings could allow greater control over your privacy.
THE ARAB SPRING: SOCIAL MEDIA AND ACTIVISM
The Arab Spring was a movement to speak out against oppression in the hope of a more democratic future across the Middle East. Starting in Tunisia in late 2010, the movement culminated in the ousting of the presidents of Tunisia and Egypt the following year.
Social media undoubtedly played a part in the Arab Spring uprising. Protesters were empowered by access to social media sites like Facebook, Twitter, and YouTube. Networks formed online were crucial in organizing the activities of a core group of activists.
Additionally, social media was used to communicate to the rest of the world what was happening on the ground during the protests. Arab Spring activists were able to use social media so effectively because the authoritarian governments of Middle Eastern countries were yet to understand the power of communicating via social media.
Bottom Line
Throughout this guide, we hope to have provided you with critical knowledge to protect your online privacy and maintain a greater level of digital security – helping to prevent your activism activities from being intercepted, secretly shared without your consent, and possibly used against you.
It’s important that activists like you – educators, journalists, human rights lawyers, healthcare workers, scientists, and civil society organizers, to name a few – can go about your causes without worrying that you’re being monitored online, that your location is being tracked, or that your devices are being hijacked.
After reading through our guide, we hope you consider something else that activist Malala Yousafzai once said: “We realize the importance of our voices only when we are silenced.”
With this in mind, our hope is that this guide safeguards your voice online – helping you to ensure your privacy and safety – and ultimately empowering you to carry on fighting for what you believe in.